this post was submitted on 08 Mar 2025
90 points (92.5% liked)
cybersecurity
3731 readers
106 users here now
An umbrella community for all things cybersecurity / infosec. News, research, questions, are all welcome!
Community Rules
- Be kind
- Limit promotional activities
- Non-cybersecurity posts should be redirected to other communities within infosec.pub.
Enjoy!
founded 2 years ago
MODERATORS
you are viewing a single comment's thread
view the rest of the comments
view the rest of the comments
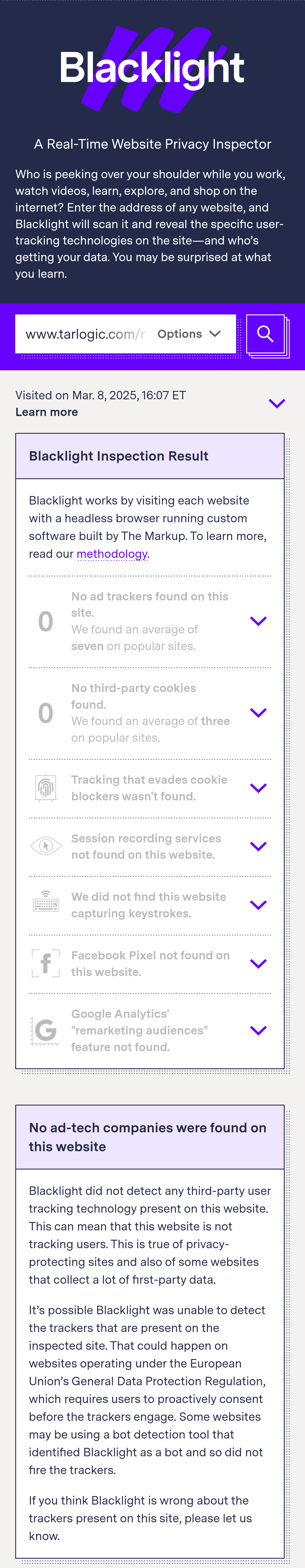
Yeah. We found the thing we were pretty sure was there!
Though, if it's really just local debug commands, then the usual "malice vs stupidity" debate is still up for grabs.