this post was submitted on 30 Dec 2024
195 points (100.0% liked)
chapotraphouse
13764 readers
726 users here now
Banned? DM Wmill to appeal.
No anti-nautilism posts. See: Eco-fascism Primer
Slop posts go in c/slop. Don't post low-hanging fruit here.
founded 4 years ago
MODERATORS
you are viewing a single comment's thread
view the rest of the comments
view the rest of the comments
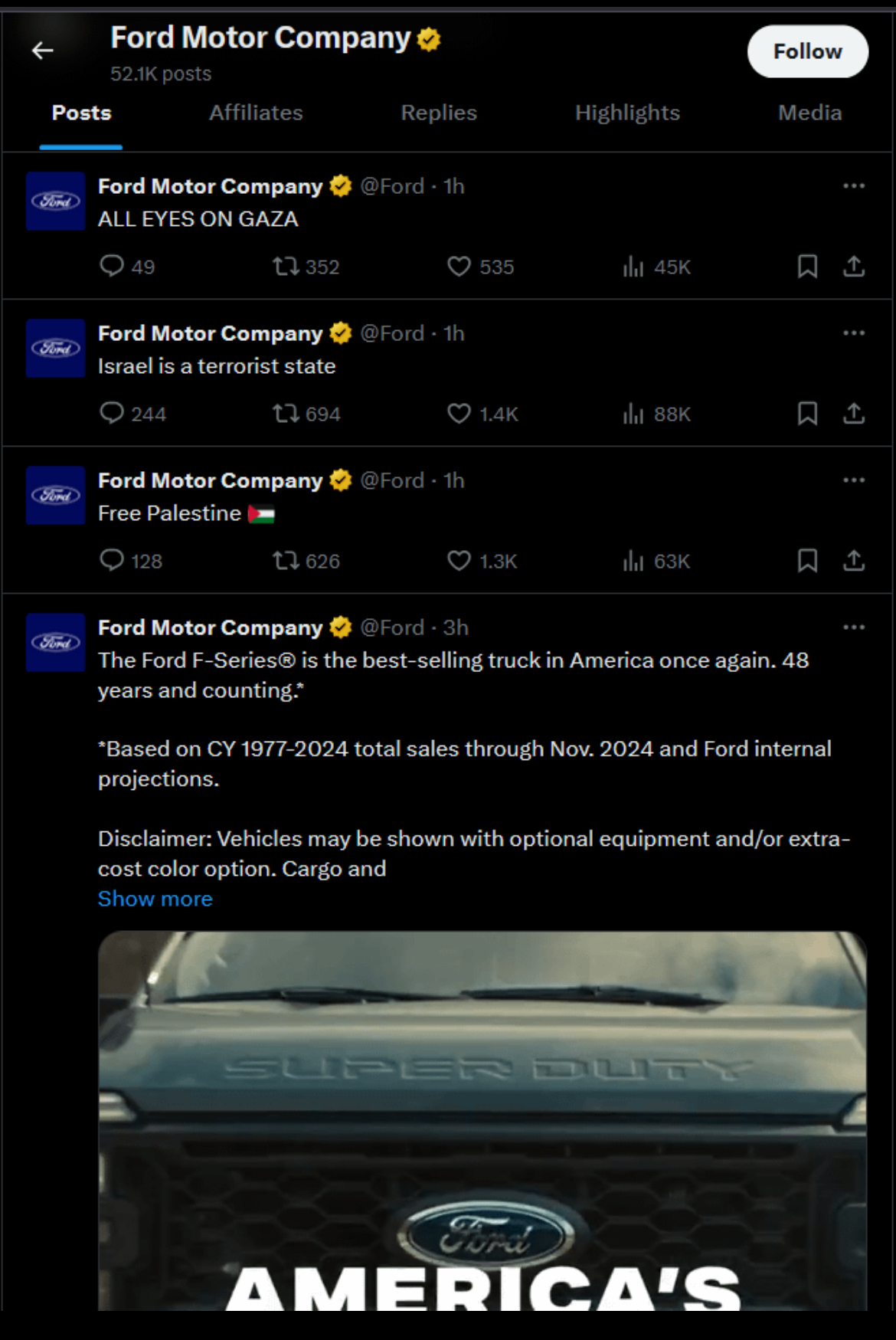
It’s not an intern. A major company at Ford’s scale does not let an intern post.
It’s likely an unauthorized access. Ford has a lot of IT security, but it’s the kind of security that is so secure, it becomes insecure (many passwords, very frequent password updates, which lead to people just writing the passwords down).
Are you saying the incoherent ramblings of my phone notes app could be compromised?
I can’t say for sure. Please post screenshots and I’ll let you know.
But it is a real Security issue, where the org has such a strict policy on ALL users to maintain a high level of security hygiene that it’s impossible to keep up with while doing normal work. It’s why there is such a big push for SSO systems/portals. As that way you can have 99% of users be kind of dumb - as long as they use your company portal - they should be good.. and a smaller team focused on the security of that portal and looking for odd login actions per user.
Requiring rotating key/authenticator access for remote work and allowing users to come up with a solid terminal password on local access is pretty good.
That way all local connections can be verified and remote logins have the extra security layer.
That being said, if a priveleged user manages to compromise their local work machine it's all fucked.
That’s where security experts who are checking for things to go bad come in.
Making everyone a security expert + doing their job is some uphill ice skating.
A good bet it to open a dummy ssh port that no one should ever connect to, then immediately add any ip that tries to connect to it to a blacklist.
At the end of the day every security measure can be bypassed, you just need to be prepared for that inevitability.
Locks are based on time/difficulty/detectability in the real world. The goal is “can’t to break in without getting caught”
It’s all a balance between risk/security and actually being useful.
I work for a company with that sort of security. It's infuriating and many people miss hours of work because they need IT's help to get back in every time there's a password change.
you worked at ford?
No.
you hacked them then?